Autonomous Mobility
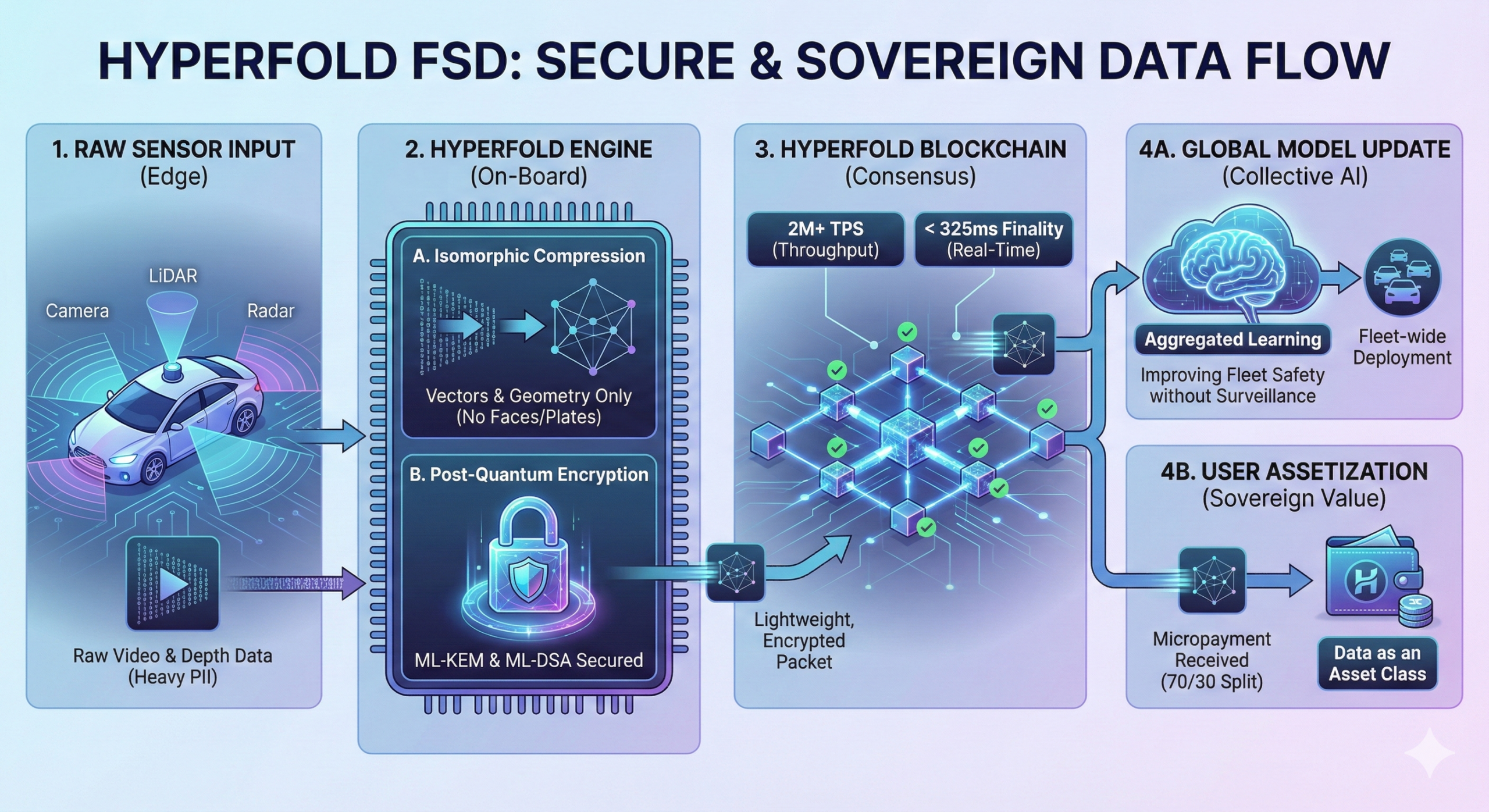
Use Case 1: The Commuter (Tesla FSD)
The Scenario: Marcus drives a Tesla Model Y. He encounters a “corner case”—a confusing construction zone with contradictory signs.
The Legacy Way (Surveillance Economy) The car gets confused and disengages. The raw video feed of Marcus’s location, his face, and his conversation is uploaded to the corporate cloud. The company uses this footage to patch their software.
- Result: The company’s stock goes up. Marcus pays a subscription fee to generate value for them. If the cloud is hacked, his travel patterns are exposed.
The HyperFold Way (The Sovereign Economy) The car detects the confusion.
- Source-Level Compression: Before leaving the car, the HyperFold protocol strips personal identifiers (faces, license plates). It compresses the geometry of the construction zone into lightweight vectors (Isomorphic Compression).
- Real-Time Consensus: The data packet is cryptographically signed with Marcus’s ML-DSA key and hits the network. Because of the 325ms finality, the network verifies the data instantly.
- Assetization: Marcus is credited for providing a high-value “edge case” dataset.
- The Result: The global driving model updates. Marcus receives a micropayment (part of the 70% split). The network knows what happened, but mathematically cannot know who Marcus is or where he went afterwards.
Autonomous Androids
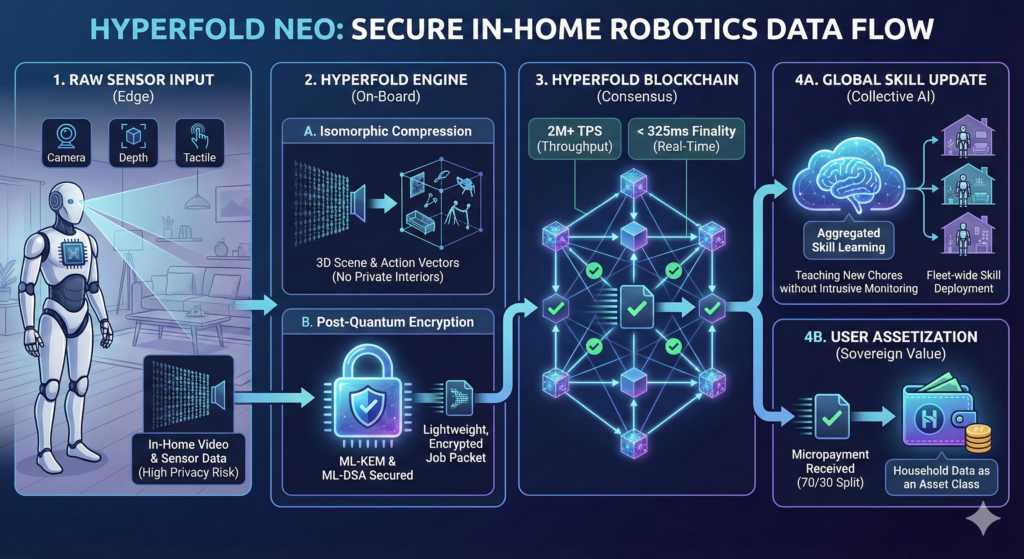
Use Case 2: The Homeowner (Neo Robot)
The Scenario: Sarah has a Neo robot in her home. It gets stuck trying to fold a fitted sheet (a complex physics problem). It needs human help via “Expert Mode.”
The Legacy Way (The “Puppet” Problem) Sarah has to accept a Terms of Service allowing a remote employee to access the robot’s cameras.
- Result: A stranger is effectively looking into Sarah’s bedroom. The video feed is stored on a centralized server “for quality assurance,” creating a permanent record of her private life. She feels watched in her own home.
The HyperFold Way (The Privacy Shield) The robot requests help.
- Isomorphic Abstraction: The HyperFold engine intercepts the camera feed. It converts the video into a 3D point cloud or “wireframe.”
- The Operator’s View: The remote expert sees a mathematical representation of the sheet and the robot’s hands. They cannot see the photos on the wall, the messy bed, or Sarah herself—only the geometry needed to solve the task.
- Quantum Security: The command stream is encrypted with ML-KEM. Even if a hacker intercepts the signal, they cannot decrypt the video feed or hijack the robot.
- Value Capture: Once the expert solves the problem, that solution becomes a training asset. Because Sarah’s robot initiated the learning instance, she owns a stake in the “Fitted Sheet Folding” module.
The Comparison Table
| Feature | The Legacy “Feudal” Model | The HyperFold “Sovereign” Model |
| Data Ownership | Corporation owns 100% | You own the keys (User Sovereign) |
| Privacy | “Trust us” (Policy-based) | Math-based (Cryptographic) |
| Video Feed | Raw, intrusive surveillance | Compressed, anonymized vectors |
| Security | Standard encryption (Vulnerable) | ML-KEM / ML-DSA (Post-Quantum) |
| Latency | Slow centralized servers | < 325ms (Real-time Edge) |
| Economic Value | You pay a subscription | You earn from the 70/30 Split |
